Different types of user accounts in Windows Server
In Windows Operating Systems, when we refer about anything as "local", we are referring about something related with that local computer. For example, when we discuss a user account as local user account, that local user account is created and stored in the Security Accounts Manager (SAM) database of the local computer. You may not be able to login with the local user account credentials from a Windows computer to another Windows computer. Please visit the following link to learn more about local user accounts and local groups in Windows Server.
Local user accounts in Windows Operating Systems can be divided into four types. 1) Standard local user accounts 2) Administrator local user accounts 3) System accounts and 4) Guest local user accounts.
Following are some common types of user accounts used in Windows Server terminology. You must remember these terms, because these terms are used repeatedly in a Microsoft Windows network environment.
- Default local user accounts
- Standard local user accounts
- Administrator local user accounts
- System accounts
- Guest local user accounts
- Active Directory domain user accounts
Default local user accounts
The default local user accounts in Windows Server are the user accounts that are created automatically by the Windows installation setup program, during the Windows Operating System installation. The default local user accounts are built–in user accounts. The default local user accounts can’t be removed or deleted. Windows Server 2025 will display an error dialog box as shown below, if you try to delete a built–in user account.
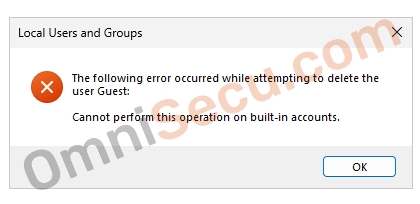
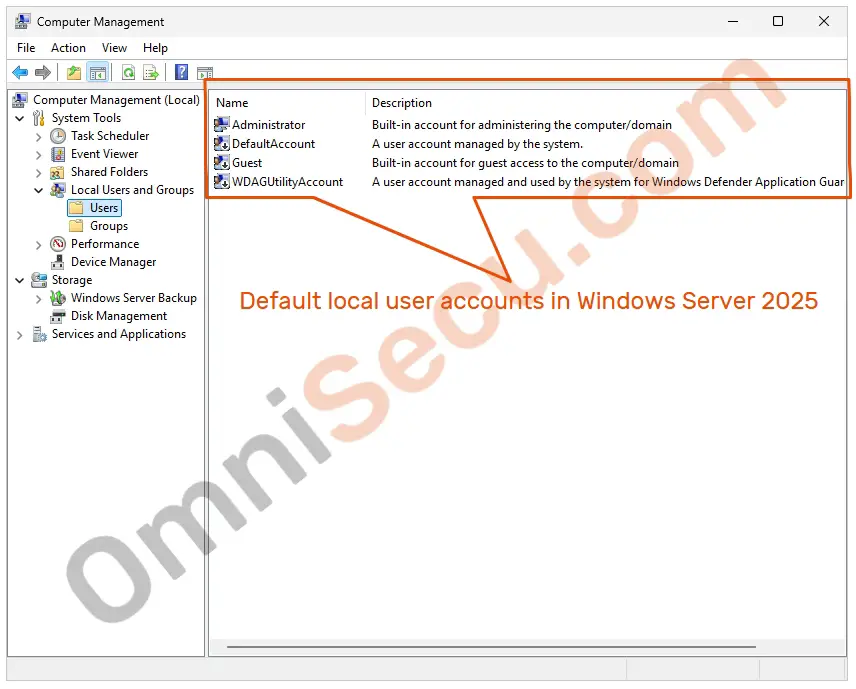
You can view the default local user accounts in Windows Server 2025 in Computer Management MMC snap–in. To open Computer Management MMC snap–in, type compmgmt.msc in Windows Run dialog box and then by click the "OK" button. Another way to open the Computer Management MMC snap–in is, search for compmgmt.msc in Windows Search box and then click the search result.
Following image shows the default local user accounts in Windows Server 2025. Please note that the below screenshot was taken just after a fresh installation of Windows Server 2025, before adding a new user or group in it.
You may run the Get-WmiObject PowerShell cmdlet as shown below, to find the default local user accounts in Windows Server, just after a fresh installation of Windows Server 2025.
PS C:\jajish> Get-WmiObject -Class "Win32_UserAccount" -Namespace "root\cimv2" | sort __CLASS,Name | Format-Table Name,caption,__CLASS Name caption __CLASS ---- ------- ------- Administrator OMNISECU-7\Administrator Win32_UserAccount DefaultAccount OMNISECU-7\DefaultAccount Win32_UserAccount Guest OMNISECU-7\Guest Win32_UserAccount WDAGUtilityAccount OMNISECU-7\WDAGUtilityAccount Win32_UserAccount
Please note that the OMNISECU-7 in the above PowerShell output is the name of the local Windows Server.
Standard local user accounts
A Standard local user account is a user account created for the end users for their day–to–day activities. A Standard local user account does not have administrative level privileges on a Windows Server 2025 based computer. Standard local users can log in locally to the Windows Operating System and perform normal user tasks like, running normal privileged programs, browse internet, print or scan etc. But they are restricted from performing administrative level tasks.
You may run the Get-WmiObject PowerShell cmdlet as shown below, to find the Standard local user accounts in Windows Server. Here, some standard local user accounts were added after the Windows Server 2025 installation.
PS C:\jajish> Get-WmiObject -Class "Win32_UserAccount" -Namespace "root\cimv2" | sort __CLASS,Name | Format-Table Name,caption,__CLASS Name caption __CLASS ---- ------- ------- Administrator OMNISECU-7\Administrator Win32_UserAccount Alex.Sam OMNISECU-7\Alex.Sam Win32_UserAccount Arjun.Dayanand OMNISECU-7\Arjun.Dayanand Win32_UserAccount DefaultAccount OMNISECU-7\DefaultAccount Win32_UserAccount Guest OMNISECU-7\Guest Win32_UserAccount Jajish.Thomas OMNISECU-7\Jajish.Thomas Win32_UserAccount WDAGUtilityAccount OMNISECU-7\WDAGUtilityAccount Win32_UserAccount
Administrator local user accounts
Local Administrator user account is the superuser of a local Windows computer. When you are logged–in to a Windows Server 2025 based computer with the local Administrator user account credentials, you can perform local system level administrative tasks. The user–id of the default Administrator user in Windows Server is Administrator. You may change the default Administrator user–id, if you wish.
You can add other Administrator user account later after the Windows Server 2025 installation, by adding a normal local user to the local Administrators group. You may run the Get-WmiObject PowerShell cmdlet similar as in the previous example, to find the default local user accounts in Windows Server 2025.
System accounts
There are many System accounts created by the Windows Server 2025 installation setup program. System accounts are used to run system services and processes and System accounts can’t be used for interactive login to a Windows Server based computer. System accounts are hidden in Computer Management MMC snap–in (compmgmt.msc), by default.
You may run the Get-WmiObject PowerShell cmdlet as shown below, to find the local System accounts in a Windows Server 2025 based computer. Please note that the Win32_SystemAccount in the __CLASS column shows that the account is a System Account.
PS C:\jajish> Get-WmiObject -Class "Win32_SystemAccount" -Namespace "root\cimv2" | sort __CLASS,Name | Format-Table Name,caption,__CLASS Name caption __CLASS ---- ------- ------- ANONYMOUS LOGON OMNISECU-7\ANONYMOUS LOGON Win32_SystemAccount Authenticated Users OMNISECU-7\Authenticated Users Win32_SystemAccount BATCH OMNISECU-7\BATCH Win32_SystemAccount BUILTIN OMNISECU-7\BUILTIN Win32_SystemAccount CREATOR GROUP OMNISECU-7\CREATOR GROUP Win32_SystemAccount CREATOR GROUP SERVER OMNISECU-7\CREATOR GROUP SERVER Win32_SystemAccount CREATOR OWNER OMNISECU-7\CREATOR OWNER Win32_SystemAccount CREATOR OWNER SERVER OMNISECU-7\CREATOR OWNER SERVER Win32_SystemAccount DIALUP OMNISECU-7\DIALUP Win32_SystemAccount ENTERPRISE DOMAIN CONTROLLERS OMNISECU-7\ENTERPRISE DOMAIN CONTROLLERS Win32_SystemAccount Everyone OMNISECU-7\Everyone Win32_SystemAccount INTERACTIVE OMNISECU-7\INTERACTIVE Win32_SystemAccount IUSR OMNISECU-7\IUSR Win32_SystemAccount LOCAL OMNISECU-7\LOCAL Win32_SystemAccount LOCAL SERVICE OMNISECU-7\LOCAL SERVICE Win32_SystemAccount NETWORK OMNISECU-7\NETWORK Win32_SystemAccount NETWORK SERVICE OMNISECU-7\NETWORK SERVICE Win32_SystemAccount OWNER RIGHTS OMNISECU-7\OWNER RIGHTS Win32_SystemAccount PROXY OMNISECU-7\PROXY Win32_SystemAccount REMOTE INTERACTIVE LOGON OMNISECU-7\REMOTE INTERACTIVE LOGON Win32_SystemAccount RESTRICTED OMNISECU-7\RESTRICTED Win32_SystemAccount SELF OMNISECU-7\SELF Win32_SystemAccount SERVICE OMNISECU-7\SERVICE Win32_SystemAccount SYSTEM OMNISECU-7\SYSTEM Win32_SystemAccount TERMINAL SERVER USER OMNISECU-7\TERMINAL SERVER USER Win32_SystemAccount
Guest local user accounts
Windows Guest user account is a special type of user account which can be used for someone accessing the computer during a short–term visit. Guest user account is disabled by default in Windows Server 2025. You can enable Guest user account from the Computer Management MMC snap–in (compmgmt.msc). It is always better to keep the Guest user account disabled for making the Windows Server more secure. There is no password for the Guest user account, by default.
Guest account does not have much computer access privileges when compared with a normal local user account.
Active Directory domain user accounts
If you are a System Administrator of a large enterprise network with hundreds of computers, it is very difficult to create, administer and maintain local user accounts in each of those computers. Active Directory domain user accounts are created in the Active Directory and stored in the Active Directory database. Active Directory domain user accounts can be used to login to any computer in that Active Directory, provided they have enough permissions to do so.
Active Directory domain user accounts are somewhat advanced level concept and we will discuss about Active Directory domain user accounts, later in another lesson.
Written by Jajish Thomas.
Last updated on 29th July, 2024.