What are IPSec Policies? Default Windows 2003 IPSec policies
IPSec policies determines which IP traffic should be secured and which IP packets should be not be secured, what type of security should be appplied to the IP packets. IPSec polices contain IPSec rules and IPSec rules contain filter lists and filter actions.
There are three default IPSec policies in Windows Server 2003. We can assign only one policy at a time.
Client (Respond Only): Client (Respond Only) IPSec policy allows the computer to attempt unsecured communications first and switch to secured communications if requested.. This policy contains the default response rule, which creates dynamic IPSec filters for inbound and outbound traffic based on the requested protocol and port traffic for the communication the system is securing.
Server (Request Security): Server (Request Security) IPSec policy configured systems can request secure IP communications whenever possible but will fall back to clear-text IP communication if non IPSec-aware computers or systems not configured using a Client (Respond Only) policy request communication.
Secure Server (Require Security): Systems configured with a Secure Server (Require Security) IPSec policy require secure communications. The filters for this policy require all communication from the given system to be secure, with the exception of the initial inbound communication request. Non IPSec aware devices and the devices which are not configured with Client (Respond Only) IPSec policy will not be able to communicate with a device configured with Server (Request Security) IPSec policy.
The default polices can be viewed at group policy editor. If you are working in a Windows 2003 Domain Controller, select Start > Programs > Administrative Tools > Domain Controller Security Policy.
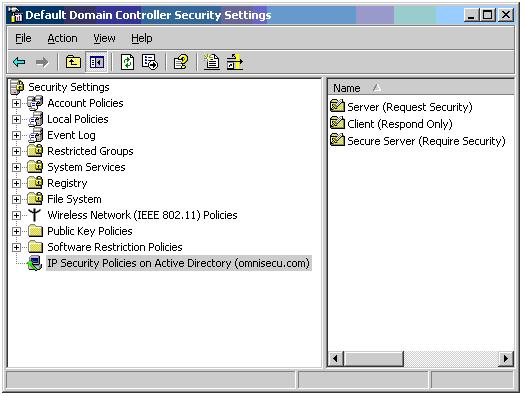
Figure 9: Domain Controller Security Policy MMC snap-in.
You have learned the three default policies with Windows Server 2003 and their functions. Click "Next" to continue.